zAccess – ZERO TRUST-BASED NETWORK ACCESS
Secure Enterprise Mobility & Seamless Access
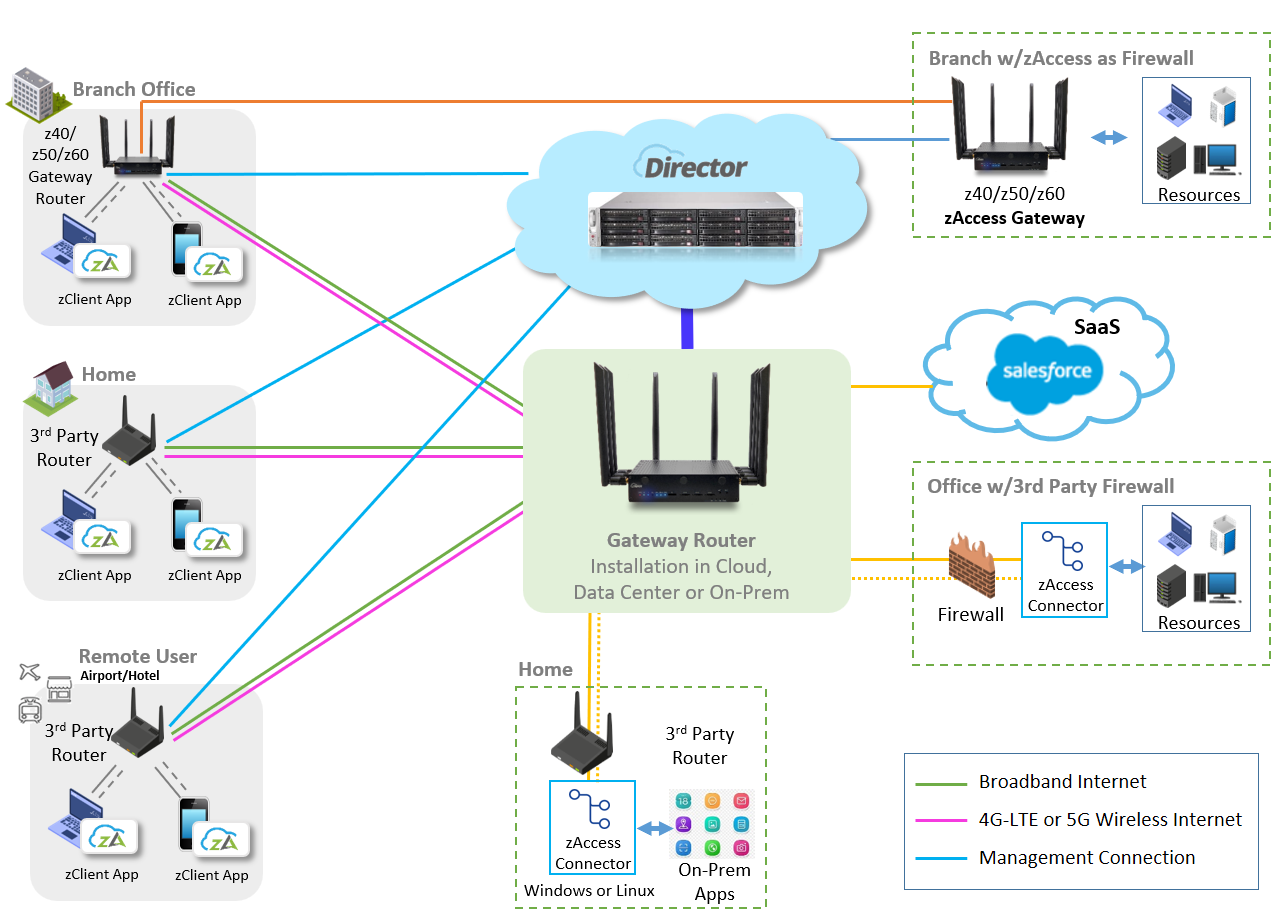
zAccess is a Zero Trust Network Access (ZTNA) solution that ensures secure and seamless access to corporate resources—including applications, servers, desktops, and network services—from any device, anywhere, and over any network. Whether users connect via trusted LANs, untrusted WANs, the internet, or mobile networks, zAccess enforces least privilege access, granting only the permissions necessary based on user roles. It continuously monitors and audits user activity in real-time, applying dynamic security policies based on identity, device health, and location to enhance security, prevent unauthorized access, and mitigate potential threats.