-
zWAN
-
-
-
-
-
-
- Articles coming soon
-
-
-
- Articles coming soon
-
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
-
-
-
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
-
-
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
-
-
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
-
- Articles coming soon
-
- IPsec Tunnel not Establishing
- SSL-VPN Tunnel not Establishing
- Mobile Network Issues
- Management Tunnel does not Establish
- DNS not Resolving from Local Network Appliance
- DNS Resolution Issues in Tunnel Configuration
- DHCP Server not Leasing IP to LAN PC
- Debugging EC Events - Unknown Status Issue
- Trusted-MAC Geofencing Issues
- DNS Issues from DC LAN PC
- Troubleshooting LAN Connectivity to Internet via WAN, Remote Branch LAN, or Local Branch LAN
- NetBalancer gateways displaying Faulty/Inactive
- Packet Drop Issues
-
-
zTC
-
- Articles coming soon
-
StorTrends
SSH Access Control List
0 out Of 5 Stars
| 5 Stars | 0% | |
| 4 Stars | 0% | |
| 3 Stars | 0% | |
| 2 Stars | 0% | |
| 1 Stars | 0% |
Overview
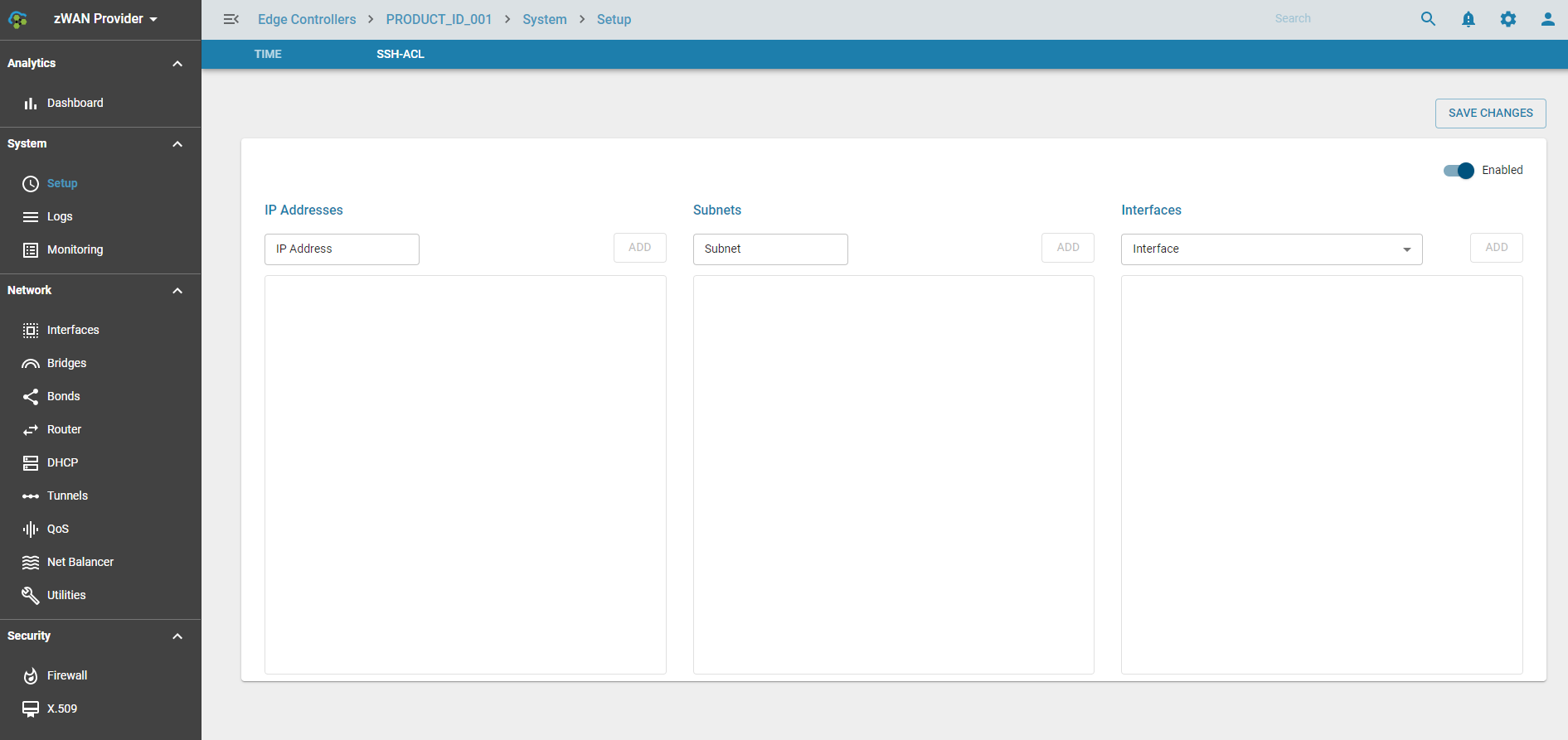
The SSH Access Control List (ACL) feature allows or restricts SSH access to the zWAN edge controller. SSH ACL configuration can be managed through the provider interface and is useful for controlled, restricted access to the device, especially for debugging purposes. SSH access can also be fully disabled if necessary.
Functionality
SSH access can be restricted based on several criteria:
- IP: Limit access to specific IP addresses.
- Subnets: Grant SSH access to specific subnets or domains.
- Interfaces: Restrict SSH access to specific network interfaces.
The image below illustrates the SSH ACL configuration interface for the zWAN edge device:
Result
Once configured, permitted IPs, subnets, or interfaces appear in the corresponding sections on the interface. By default, all connections are allowed if the SSH ACL is not enabled. When enabled, only traffic from specified IPs, subnets, or interfaces will be permitted to access the edge controller.
Known Limitations
- Subnet Validation: The system does not validate subnet entries, so users must ensure they enter correct subnet details.
- IPv6 Support: IPv6 addresses are not validated.
0 out Of 5 Stars
| 5 Stars | 0% | |
| 4 Stars | 0% | |
| 3 Stars | 0% | |
| 2 Stars | 0% | |
| 1 Stars | 0% |