Geo-Fencing
Geofencing is a security feature that defines a virtual boundary for a device’s operational area. When this boundary is breached, the device’s functionality halts.
Overview
Trusted MAC Address-based geofencing allows the edge controller to operate only when certain trusted MAC addresses are detected. This feature, under the Security section, currently activates only during the boot-up process.
Trigger Conditions
Trusted MAC Address-based geofencing activates at boot-up if:
- Any mandatory trusted MAC address is missing.
- The number of discovered trusted MAC addresses is below the configured threshold.
Functionality
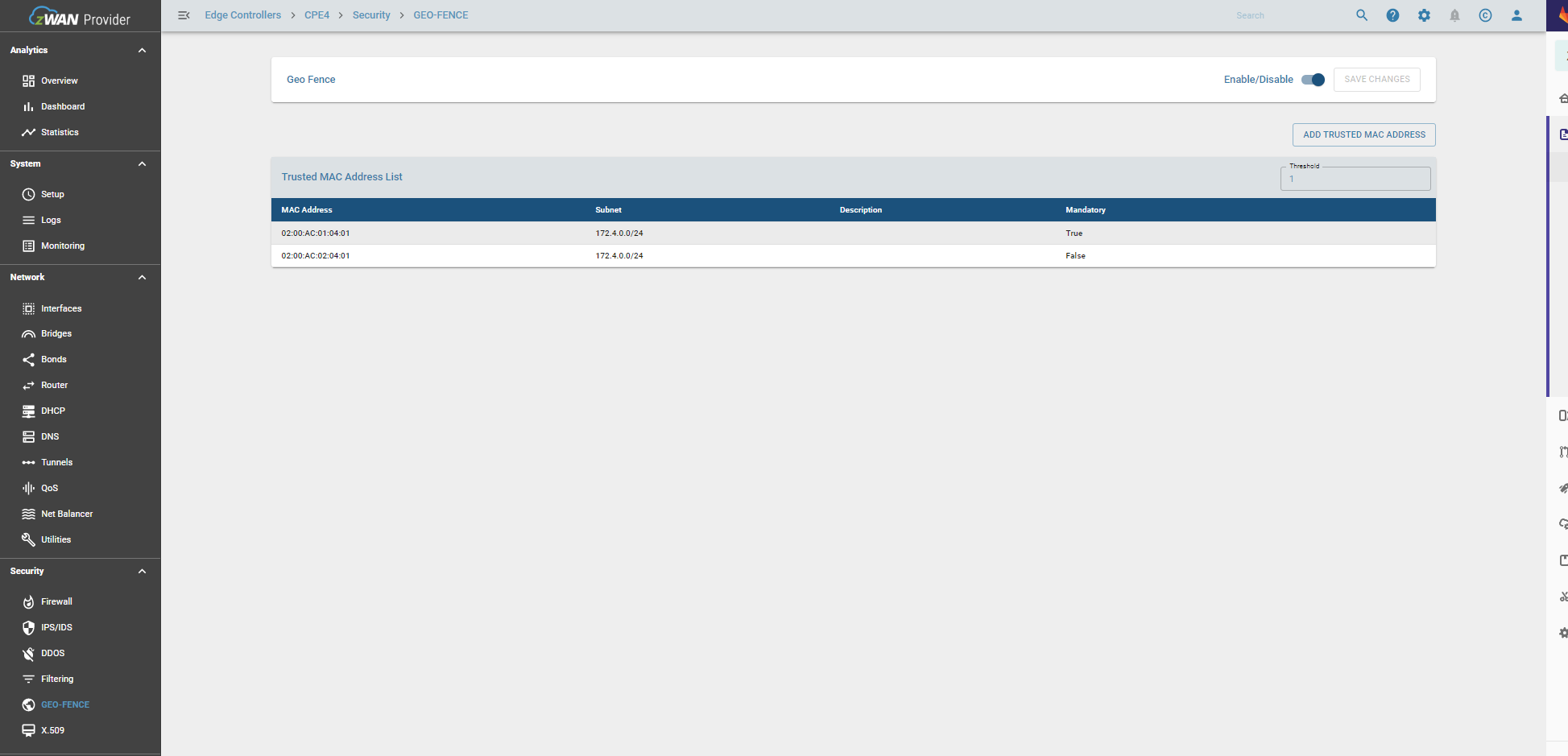
After updating the trusted MAC configuration, “SAVE CHANGES” must be executed. The main functionalities include:
Enable/Disable Geofence
Geofencing can be enabled through the enable button. At least one trusted MAC address must be added to activate geofencing.
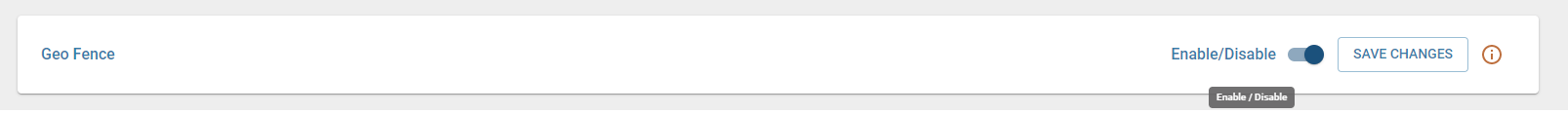
Add Trusted MAC Address
- Manual Entry – Enter the MAC address, subnet, and (optional) mark it as mandatory. If a mandatory MAC address is not detected during reboot, geofencing activates, shutting down data flow.
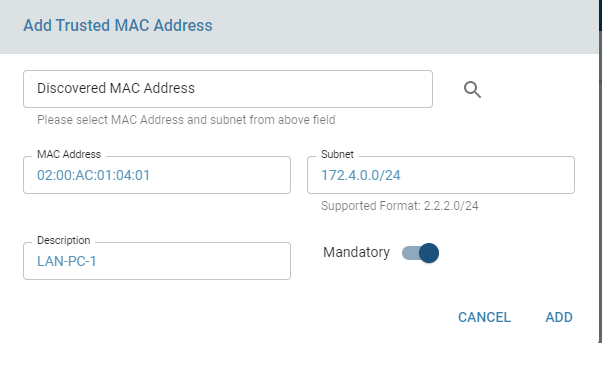
- Discover Local LAN MAC Addresses – Start MAC discovery across LAN networks. After discovery completes, select a MAC address from the dropdown to populate fields automatically.
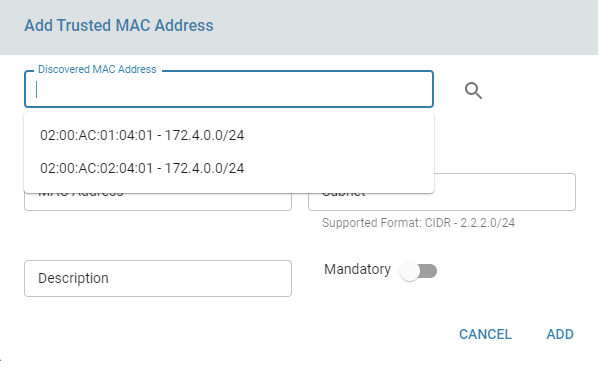
Configure a threshold count for detected MAC addresses to prevent shutdown. This count cannot exceed the total number of trusted MAC addresses added.

Delete MAC Address
Remove any listed MAC address using the delete button and confirm changes by saving.
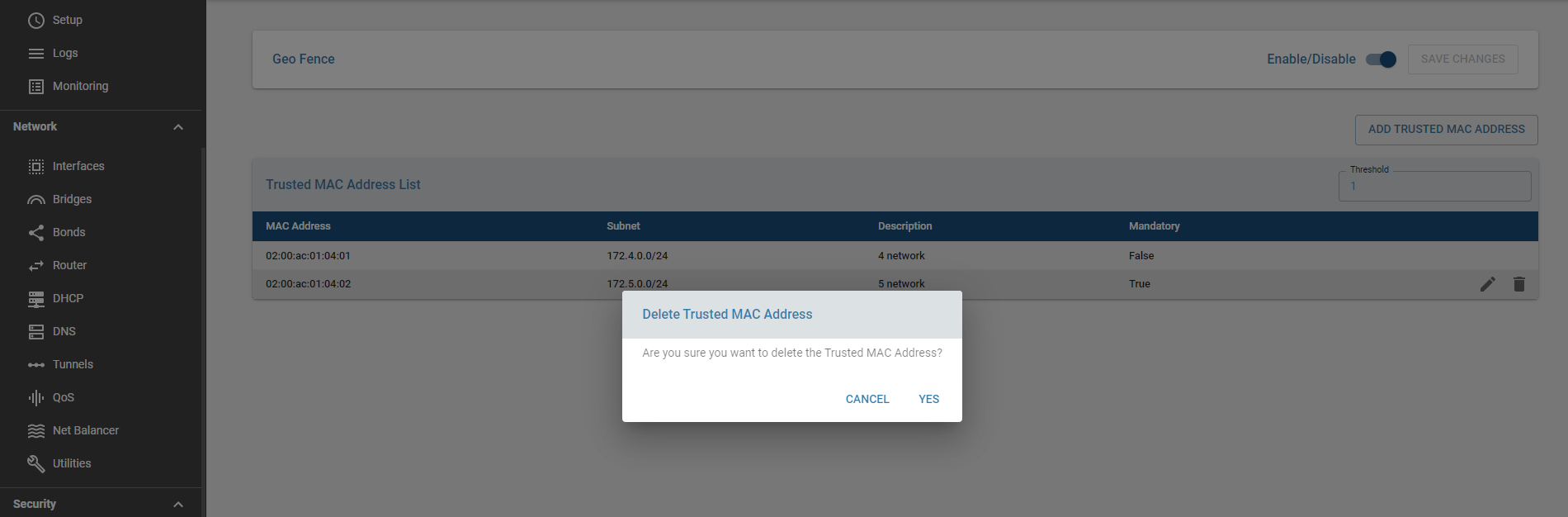
Only saved changes are applied to the edge controller. Unsaved changes display a warning icon.
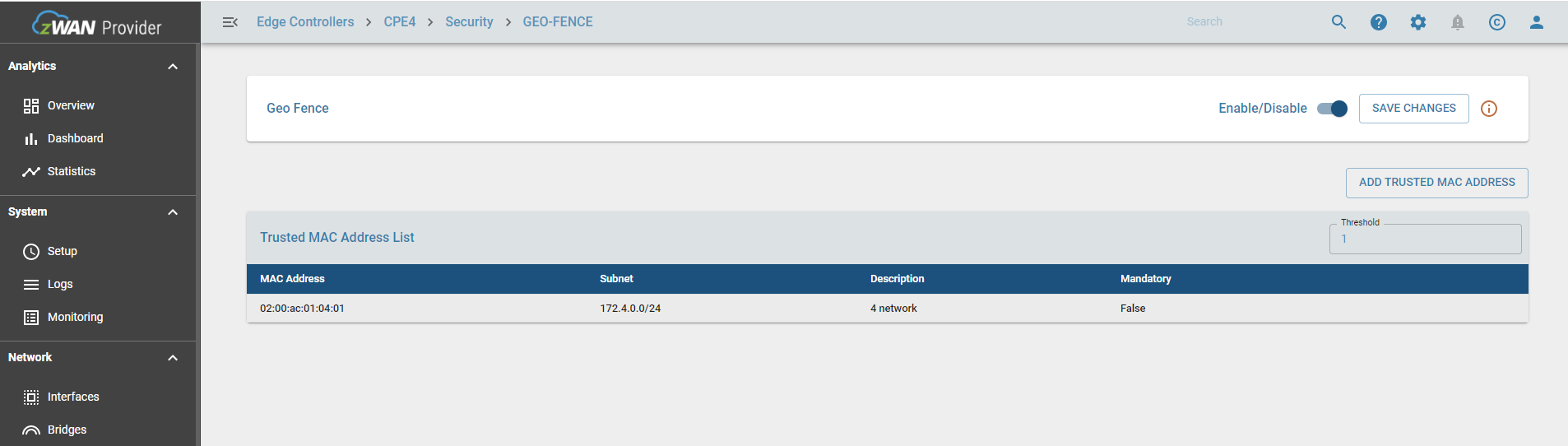
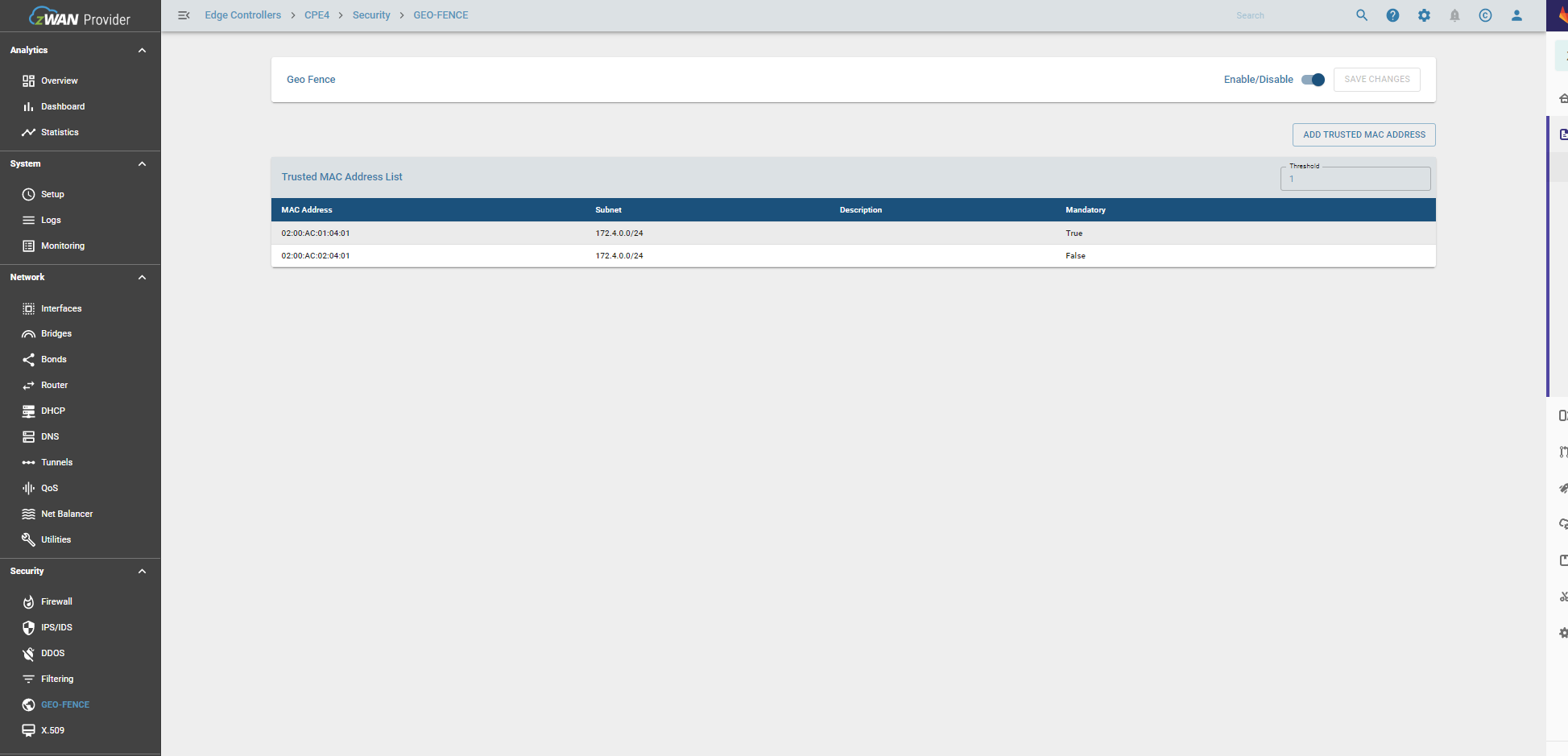
Result
Once configured, the trusted MAC addresses display as below:
If conditions are unmet post-reboot:
- Alerts and ELK dashboard notifications are generated.
- CPE logs display detailed messages.
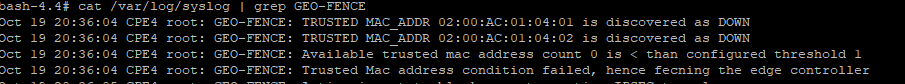
Log for missing mandatory trusted MAC address:
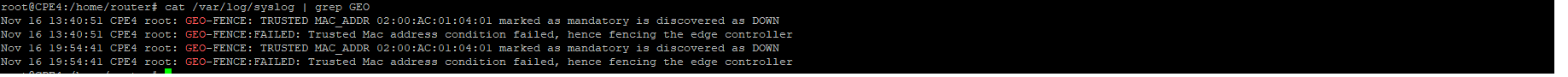
Known Limitations
- Only supports Trusted MAC Address-based geofencing.
- Activated only during system reboot.
Future Enhancements
- Additional geofencing features (e.g., WiFi-based, LTE-based).
Overview
The GPS Location-based Geofence feature, found in the Security section, provides an added security layer for the edge controller by defining geographic boundaries. Currently, geofencing is applied only during the edge controller’s boot-up process.
Trigger Condition
The GPS-based geofencing triggers under the following condition upon boot-up:
- If the current GPS coordinates fall outside the preconfigured GPS location boundary.
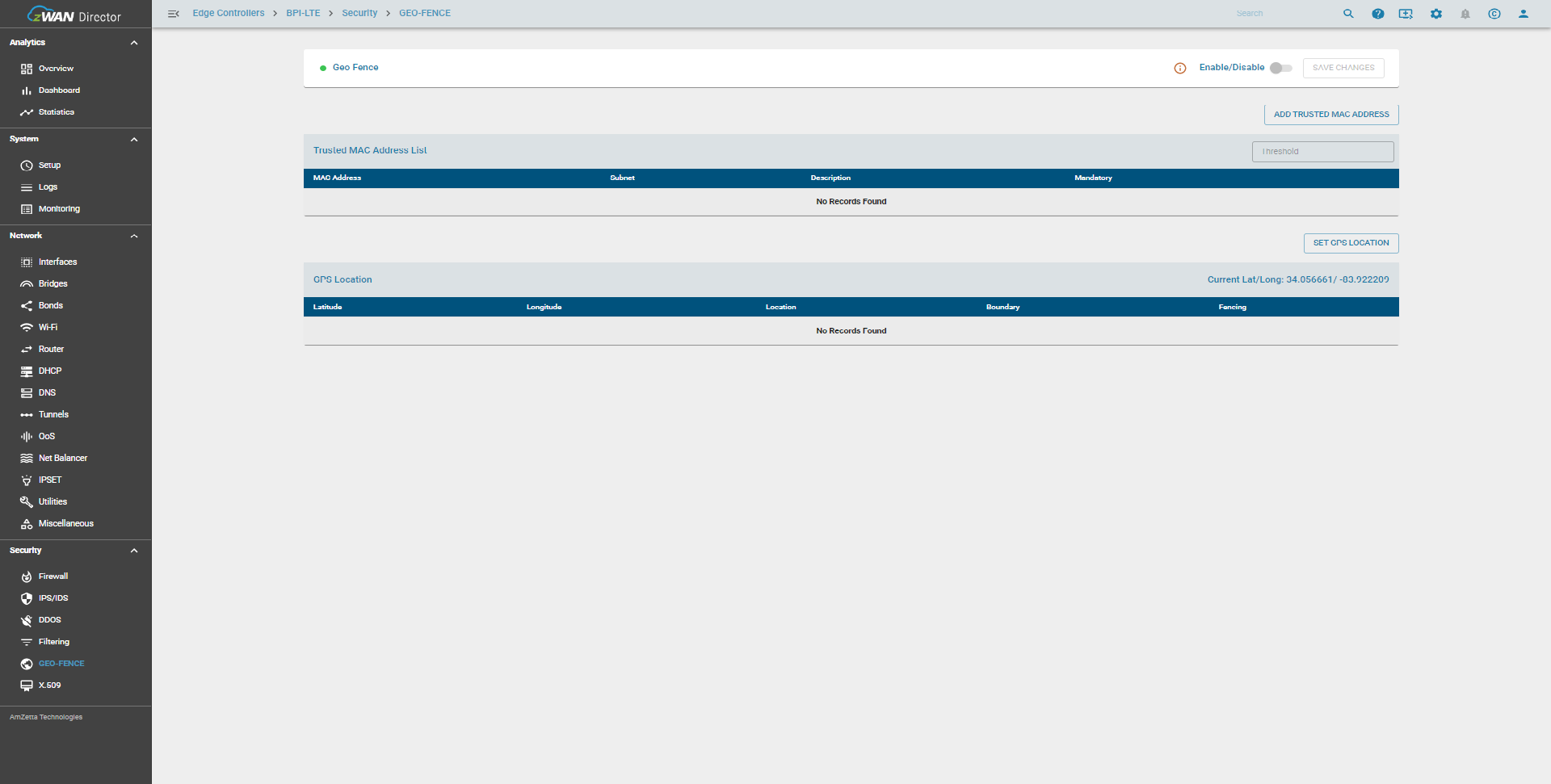
Functionality
When updating GPS location settings, users must execute “SAVE CHANGES” to apply configuration updates. The main functionalities include:
Enable/Disable Geofence
To activate geofencing, use the enable button. Note that at least one geofencing mode must be configured, either by:
-
- Adding a trusted MAC address
- Configuring a GPS location boundary

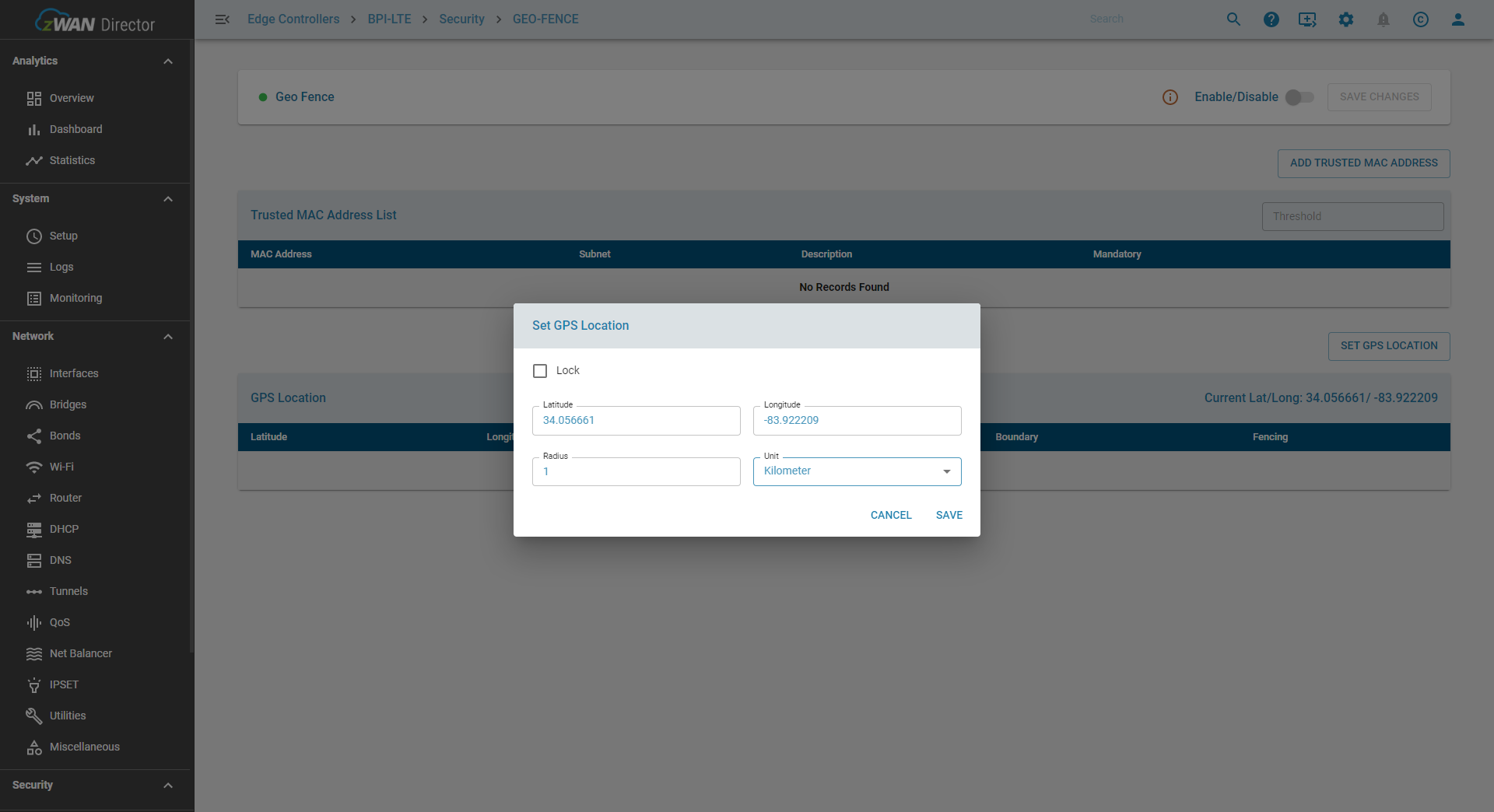
Set GPS Location
Configure a GPS boundary through one of two options:
-
-
- Manual Entry – Enter Longitude, Latitude, and Radius (in kilometers or miles). An optional “Lock” setting enforces the geofence restriction when selected.
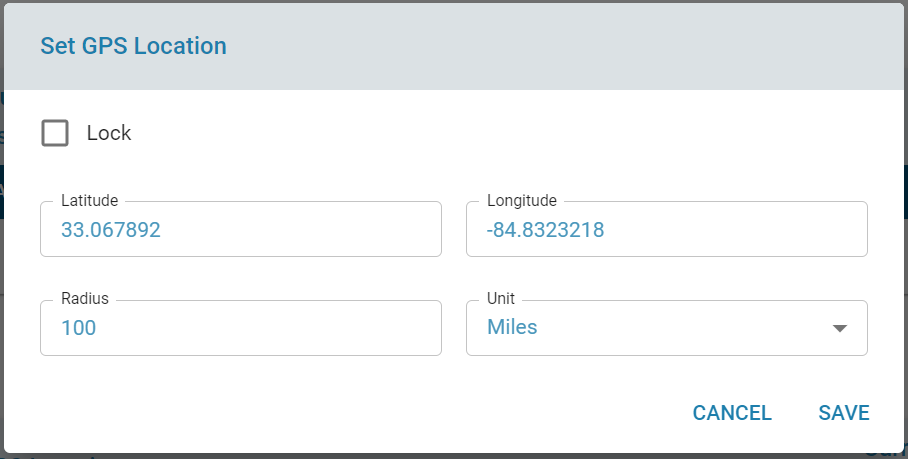
- Populate Current GPS Location – If the LTE connection provides location data, click “Set GPS Location” to auto-fill the current GPS coordinates. The default Radius is set to 1 kilometer. Fields are editable, and enabling “Lock” enforces the geofence restriction.
- Manual Entry – Enter Longitude, Latitude, and Radius (in kilometers or miles). An optional “Lock” setting enforces the geofence restriction when selected.
-
Once configured, click Save to store the GPS location, then Enable and finally SAVE CHANGES in the top-right corner to apply the configuration. Unsaved changes will show a warning icon.
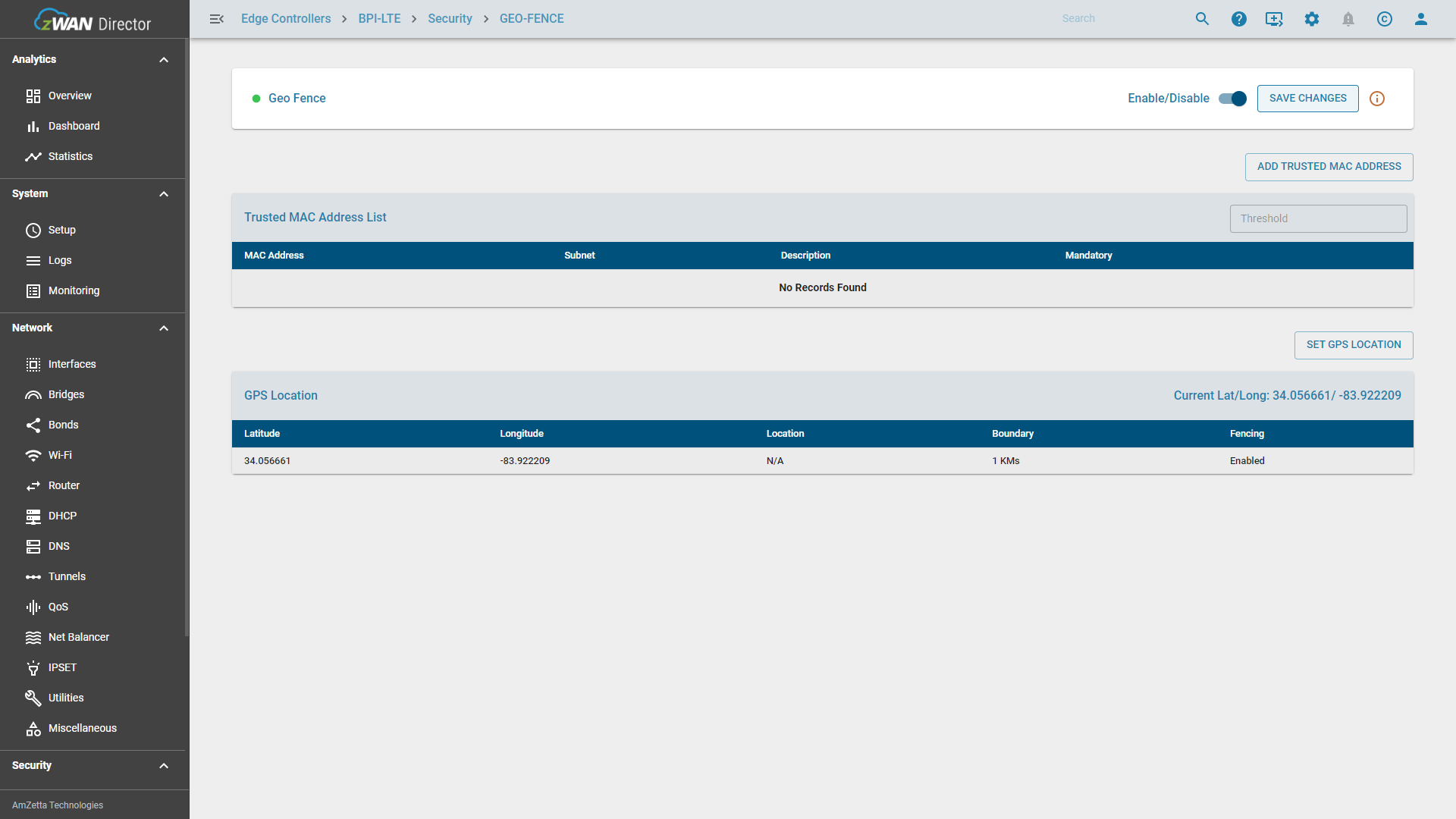
Result
Upon configuring and saving the GPS geofence, the page will display the applied settings:
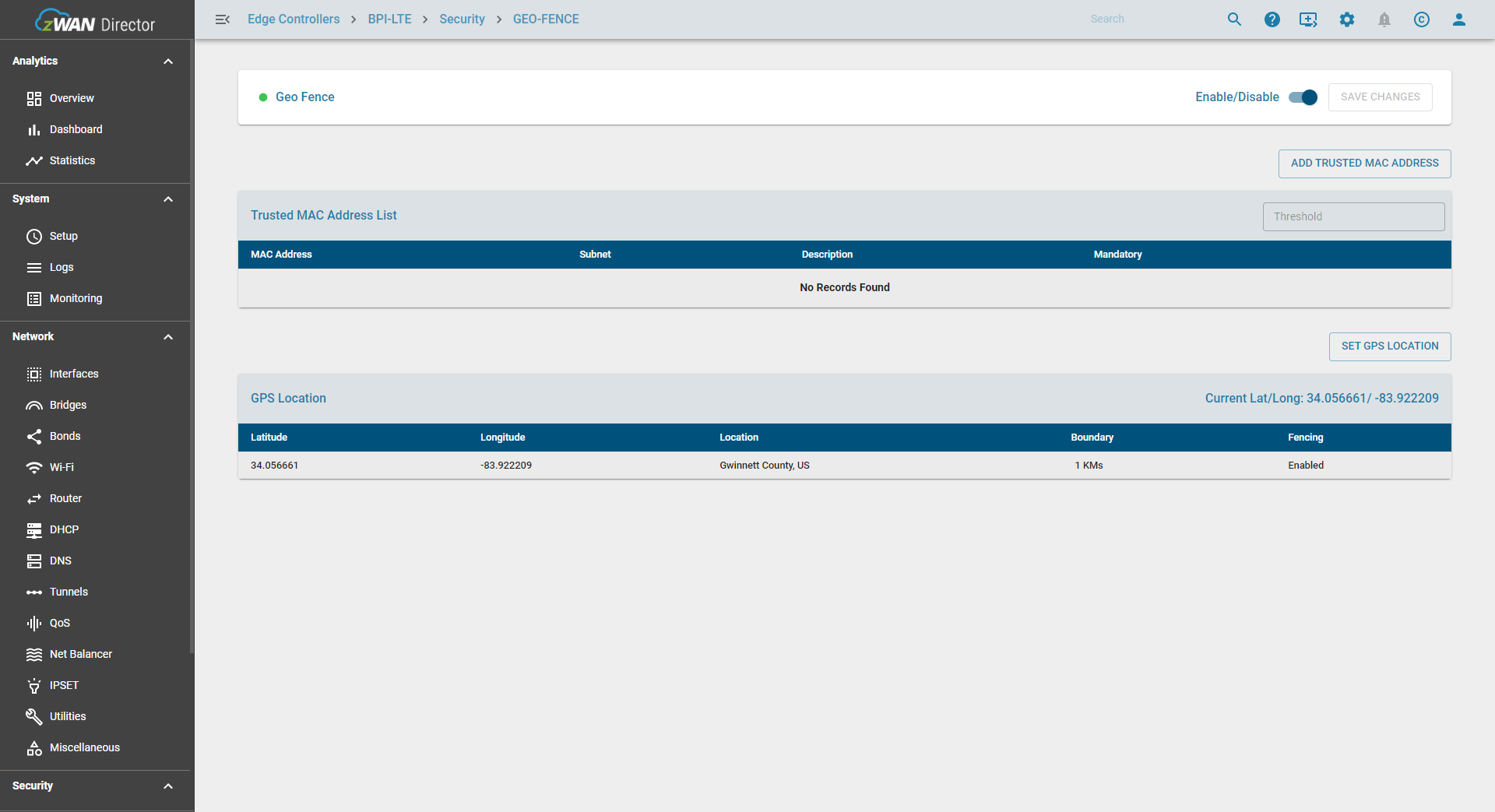
Alerts and Logging
If, after reboot, the device is outside the configured GPS boundary:
-
-
- Alerts are triggered if configured.
- Notifications appear in the ELK dashboard.
- Logs display relevant messages in the CPE log.
-
Known Limitations
-
- Geofencing is enforced only if real-time GPS location data is available.
- This feature activates only upon a system reboot.