-
zWAN
-
-
-
-
- Firewall & Layer 7 Application Filtering
- VPN Site-to-Site Tunnel Setup & Connectivity (z40 to Cloud vGR)
- Intrusion Prevention System (IPS) / Intrusion Detection System (IDS) Testing
- DNS Filtering
- DDoS Protection & Logging
- MAC Address Filtering & Geo-fencing
- Application Control & Protocol Blocking
- Authentication & Access Control (zID)
-
- WAN Link Failover & Load Balancing (ACI Mode)
- Dynamic Path Selection & Application-Aware Routing
- SaaS & Internet Breakout Validation
- QoS for Microsoft Teams (Datacenter vGR + Branch z40)
- Tunnel Failover (z40 ↔ vGR) — WAN00 (wired) primary, WAN03 (4G) & WAN04 (5G) backups
- IP Routing & Static Route Steering (z40 Branch)
- VLAN & Layer-2 Bridging
-
-
-
-
-
-
- Articles coming soon
-
-
-
- Articles coming soon
-
- Articles coming soon
-
-
-
-
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
-
-
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
-
-
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
- Articles coming soon
-
-
-
- Articles coming soon
-
- IPsec Tunnel not Establishing
- SSL-VPN Tunnel not Establishing
- Mobile Network Issues
- Management Tunnel does not Establish
- DNS not Resolving from Local Network Appliance
- DNS Resolution Issues in Tunnel Configuration
- DHCP Server not Leasing IP to LAN PC
- Debugging EC Events - Unknown Status Issue
- Trusted-MAC Geofencing Issues
- DNS Issues from DC LAN PC
- Troubleshooting LAN Connectivity to Internet via WAN, Remote Branch LAN, or Local Branch LAN
- NetBalancer gateways displaying Faulty/Inactive
- Packet Drop Issues
-
-
zTC
-
-
-
-
-
- Citrix HDX + USB Headset (Call-Center Baseline)
- VMware Horizon + Smart Card / CAC Login
- Microsoft AVD/RDP + Teams Optimized Video
- Multi-Monitor & 4K Performance
- USB Device Management - Block Storage
- Printing to Local USB & Network Printers
- Barcode Scanner (HID) with Line-of-Business App
- Kiosk / Assigned-Access Auto-Launch
- Wi-Fi Roaming & Link Change Mid-Session
- Power Management and Session State
- OS/Firmware Update & Rollback
-
-
StorTrends
-
zAccess
-
zGuardian
Firewall
0 out Of 5 Stars
| 5 Stars | 0% | |
| 4 Stars | 0% | |
| 3 Stars | 0% | |
| 2 Stars | 0% | |
| 1 Stars | 0% |
Overview
zWAN offers a basic stateful firewall for packet filtering. Packets can be filtered based on multiple conditions such as tuples, applications, time, fully qualified domain names (FQDNs), and web categories.
Functionality
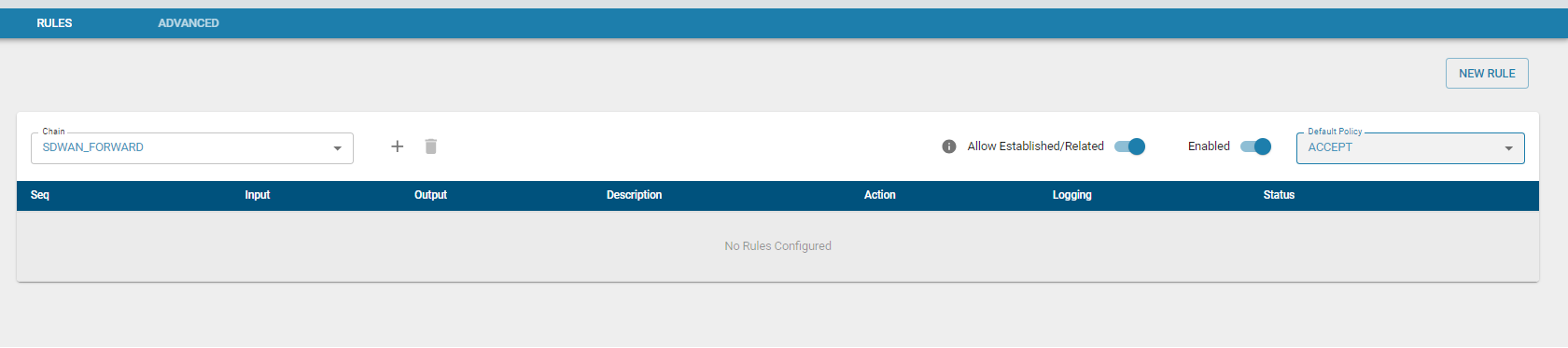
The flow classifier module is used to configure firewall rules, determining whether to ACCEPT, DROP, REJECT, RETURN, or jump to a user-defined chain.
Rules can be configured for two types of traffic:
- SDWAN_INPUT – Rules determine which inbound traffic will be accepted or denied.
- SDWAN_FORWARD – Rules determine which forwarded traffic will be accepted or denied.
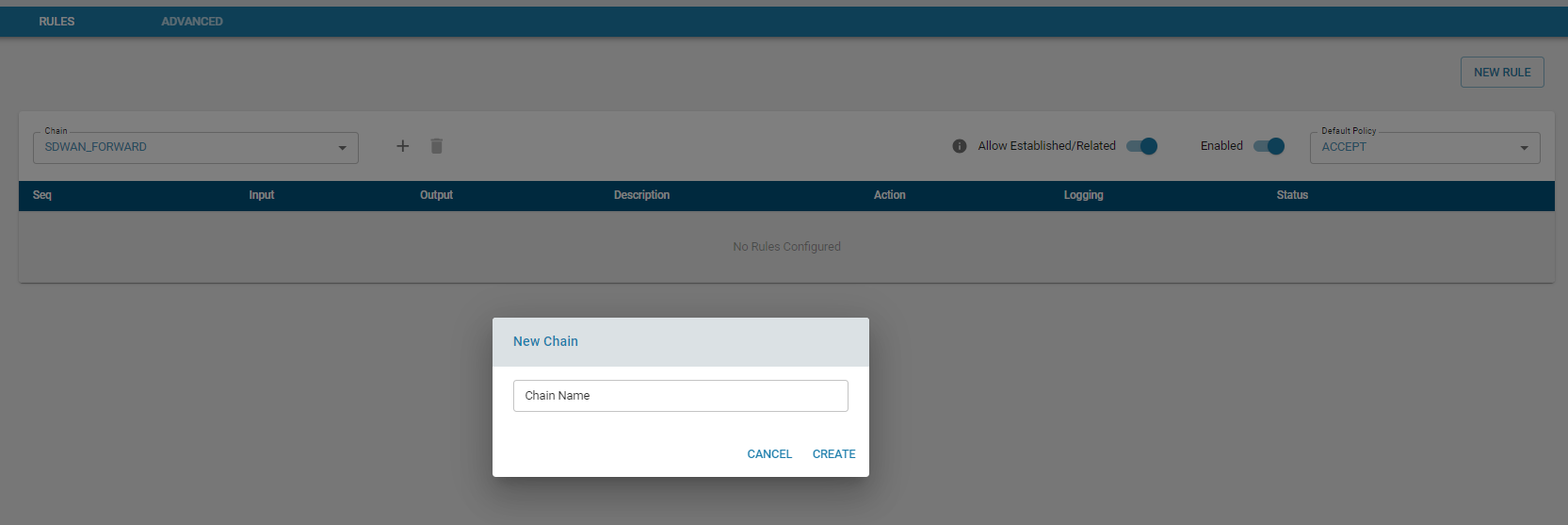
Users can also create custom chains and link them to the default chains mentioned above.
Add Chain
Add Rule
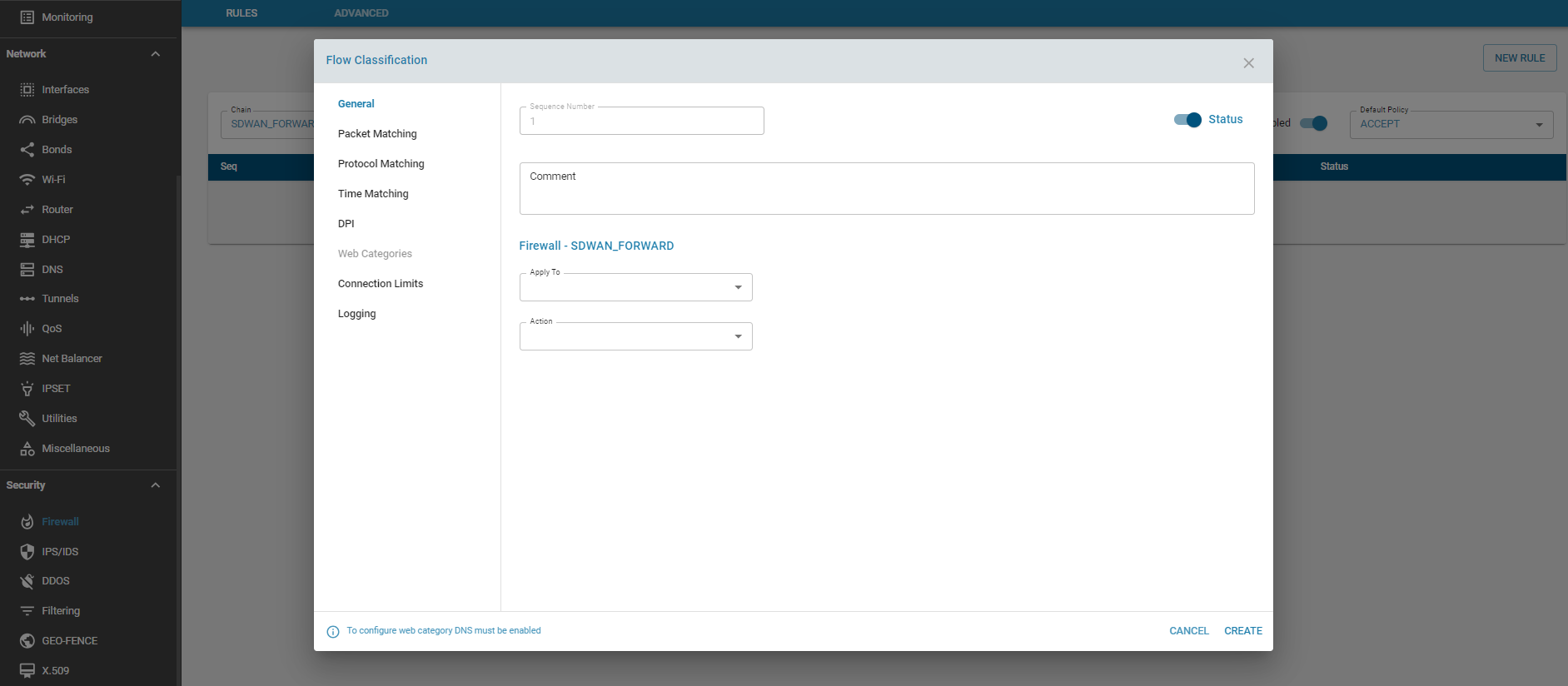
Action Types
- ACCEPT – Packets matching the filter are accepted and not checked against subsequent rules.
- DROP – Packets matching the filter are dropped without notifying the sender.
- RETURN – Packets are sent back to the originating chain for further rule processing.
- REJECT – Packets are rejected, and an error message is sent to the sender.
- CHAIN – Packets are forwarded to a custom chain for further rule processing.
Default Policy
If a packet does not match any firewall rules, the system applies the default policy for that chain, which is either ACCEPT or DROP. If a rule does not specify a target, it follows the default chain policy.


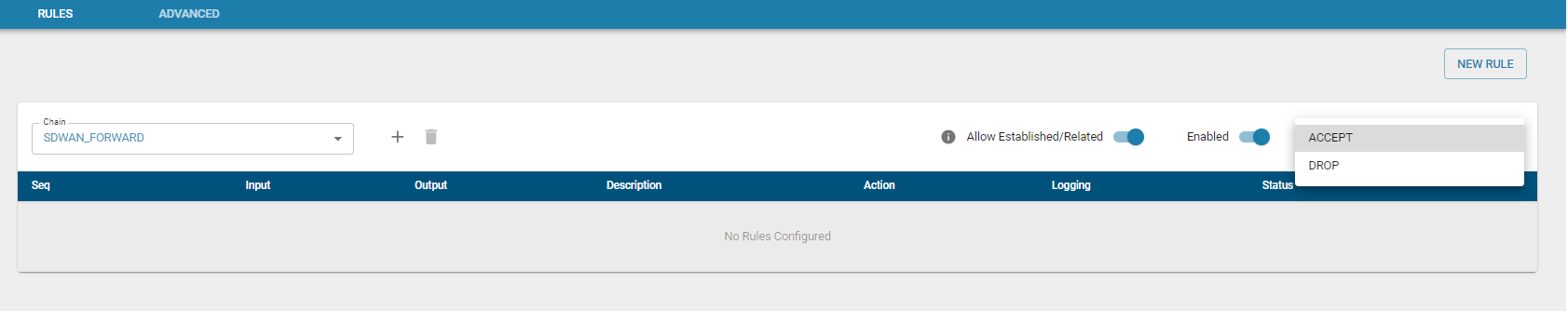
 firewall_defaultpolicy_types.png” alt=”Default Policy” />
firewall_defaultpolicy_types.png” alt=”Default Policy” />
Established / Related Connections
The firewall tracks established connections to optimize processing:
- Established: Packets belong to an existing connection and are automatically allowed.
- Related: Packets are new but associated with an existing connection and are permitted.
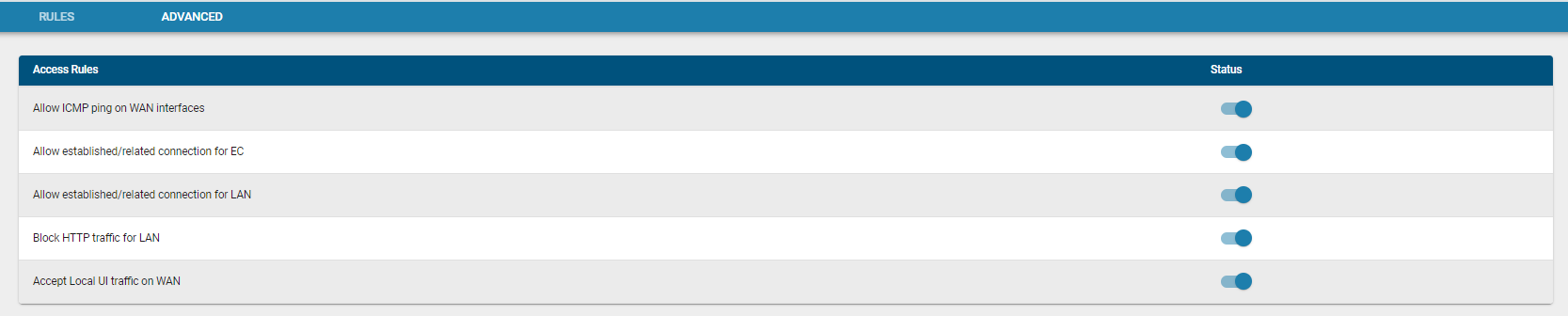
Advanced Options
Users can enable or disable global firewall settings, such as:
- Blocking HTTP traffic
- Blocking ICMP ping on WAN interfaces
- Allowing local user interface traffic on WAN interfaces

Usage
The firewall is designed to prevent unauthorized access to or from an external network, ensuring secure communication.
Known Limitations
Some functionalities may be restricted based on the zWAN hardware or software configuration.
0 out Of 5 Stars
| 5 Stars | 0% | |
| 4 Stars | 0% | |
| 3 Stars | 0% | |
| 2 Stars | 0% | |
| 1 Stars | 0% |