Profile Management
Device Profiles determine a security trust level of a connecting device and then authorize application access to the device. Device profile is a set of Host Scan policies and an access control list.
Device Profiles overrides (or say restricts) the applications access over the applications in the Application Groups. VPN Administrator can create three types of Security Profiles:
Mandatory Profile
Quarantine Profile
Normal Profile
zGateway Administrator can create only one Quarantine Profile and Mandatory Profile and multiple Normal Profiles.
MANDATORY PROFILE
This is a system profile which contains a subset of policies that must be satisfied by all connecting endpoints before the user can login into zGateway server. Using mandatory profile, administrators can enforce that the connecting endpoint must comply with certain requirements. An example of Mandatory Profile would be enforcing login using company laptops/desktops only from certain branch office only. Only one mandatory profile is allowed. If the endpoint machine fails any of the policies of Mandatory Profile, the user is denied login into zGateway server. Appropriate remediation information is sent to the user.
A normal device profile policy must exist before a mandatory profile can be created. Mandatory profile does not contain any access list as it will only enforce the selected host scan policies on all devices.
QUARANTINE PROFILE
This profile, when present, will be used for endpoints which fail to fall under any other profiles. This is an optional system profile which does not contain any policies but just list of application which the user can access if the endpoint falls in this profile. If no quarantine profile exists and the user does not satisfy any other profile, then user is denied login into zGateway server.
A normal device profile policy must exist before a quarantine profile can be created. A Quarantine profile does not contain any Host Scan policy list as it is a fallback, no-scan profile.
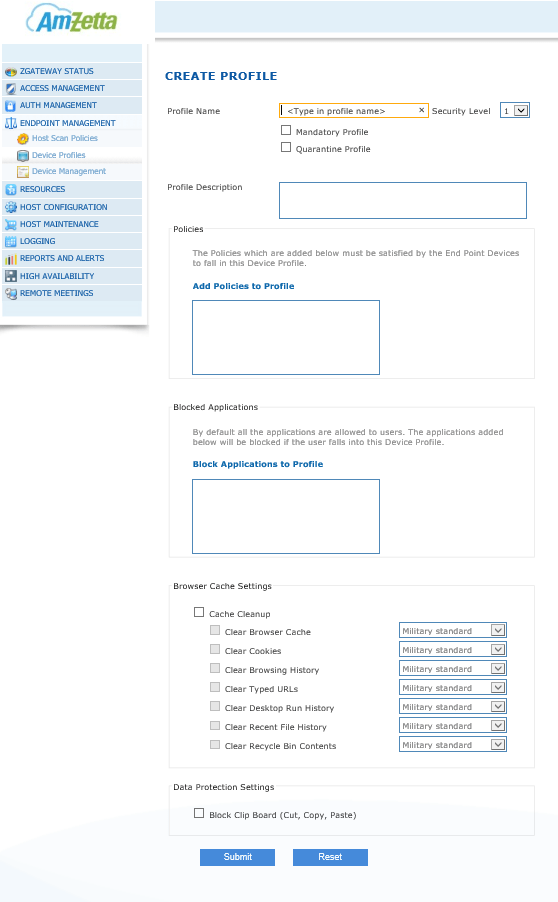
CREATE PROFILE
On the zGateway management console, expand Endpoint Management > Device Profiles. Click Add to create a new profile.
Profile Name: Profile identifier.
Security Level: Security Trust Level Identifier. Lower value means higher security trust level. An endpoint is always scanned again descending order of security trust level.
Mandatory Profile: To create Mandatory Profile, click on the check box for Mandatory Profile. If Mandatory Profile is already created then this field will be disabled. You can create only one Mandatory Profile.
Quarantine Profile: To create Quarantine Profile, click on the check box for Quarantine Profile. If Quarantine Profile is already created then this field will be disabled. Only one Quarantine Profile can be created. The Endpoint machine which fails EPS scanning will fall into this profile.
Profile Description: Enter Profile description.
Click on the Add Policies to Profile link to add policies to this profile (see the next section Add Policies to Profile for more information). The Policies which are added here must be satisfied by the End Point Devices to fall in this Device Profile.
Click on the Block Applications to Profile link to block applications to this profile. By default all the applications are allowed to users. The applications added here will be blocked if the user falls into this Device Profile.
Browser Cache Settings: When enabled zGateway will cleanup cache created by browser or other components after logout from server.
Clear Browser Cache – Delete temporary internet files created by browser
Clear Cookies – Delete stored browser cookies
Clear Browsing History – Delete history of visited links
Clear Typed URLs – Delete history of URLs typed by user
Clear Desktop Run History – Delete the command executed by user from Run menu item of start menu in Windows.
Clear Recent File History – Delete the history created by Windows for recently opened files
Clear Recycle Bin Contents – Delete all data in recycle bin
Data Protection Settings: If enabled, on a device falling under this profile, access to clipboard will be disabled to the user and applications running on the endpoint.
Click Submit to create the Security Profile or click Reset to clear all data from this screen.
A success message confirms that the Security Profile has been created.
ADD POLICIES TO PROFILE
When creating a Device Profile, you can add policies to it using these steps:
On the Create Profile screen, click on the Add Policies to Profile link. The Add Policy to Profile screen appears.
Select the policies in the left table that you want to apply to this profile and click Add. The selected policies move from the left table to the right side table on the screen.
Click Submit to select the policies for this profile, or click Cancel to abort.
The popup window will close and the name of the policies will appear in the Policies box on the Create Profile page.
Click Submit to save changes or click Reset to remove all data from the screen.
NB: Changes to Profile are not applied until after you have clicked the Submit button on the Create Profile or the Modify Profile screen.
BLOCK APPLICATIONS TO PROFILE
When creating a Device Profile, you can add applications to be blocked using these steps:
On the Create Profile screen click on the Block Applications to Profile link. The Add/Block Applications to/from Profile screen appears.
Select the applications in the Applications table that you want to block and click Add. The selected applications move from the Applications table on the left side to the Selected Applications table on the right side of the screen.
Click Submit to select the applications for this profile, or click Cancel to abort.
The popup window will close and the name of the applications will appear in the Applications box on the Create Profile page.
Click Submit to save changes or click Cancel to remove all data from the screen.
NB: Changes to Profile are not applied until after you have clicked the Submit button on the Create Profile or the Modify Profile screen.
MODIFY PROFILE
On the zGateway management console, expand Endpoint Management > Device Profiles.
Type the profile name in the Search Profiles field. If entering multiple names, separate names with a comma. Type [*] to view all profile names.
Click Show to view the search results.
Click on the check box for the profile you want to edit and click Modify. The Modify Profile screen appears. Modify profile details as needed. Refer to Create Profile section while making the entries.
Click Modify to save changes or click Cancel to cancel the changes made.
DELETE PROFILE
In the Edit Profile screen described above, click on the box for the Profiles you want to delete. To select all profiles, click on the Check all check box below the table.
Click Delete to delete the selected profiles.
When prompted for deletion confirmation, click OK to delete the profiles or click Cancel to abort.
EXAMPLE OF END USER NOTIFICATION WHEN FAILING ENDPOINT SECURITY SCAN
When a user logs in the Endpoint Scan initiates and displays any warnings or restrictions to the user.